Using AI to automate threat and risk assessments
RL
Overview
This week I decided to test the ‘ContextCypher’ application by Threat Vector Security. This application promises to integrate with AI to achieve automated threat and risk assessments. This is quite close to the work that I’ve been performing for several years now, so I decided to give it a go.
ContextCypher -What it does
This application is a local app which a user runs on their Operating System(OS) of choice and then connects it to their LLM of choice, either a local LLM such as Llama 3.1:8b (which I ran locally using Ollama) or else using their API based LLM of choice. I also decided to test using OpenAI gpt-4o.
Once opened and connected to AI, the app looks like this:
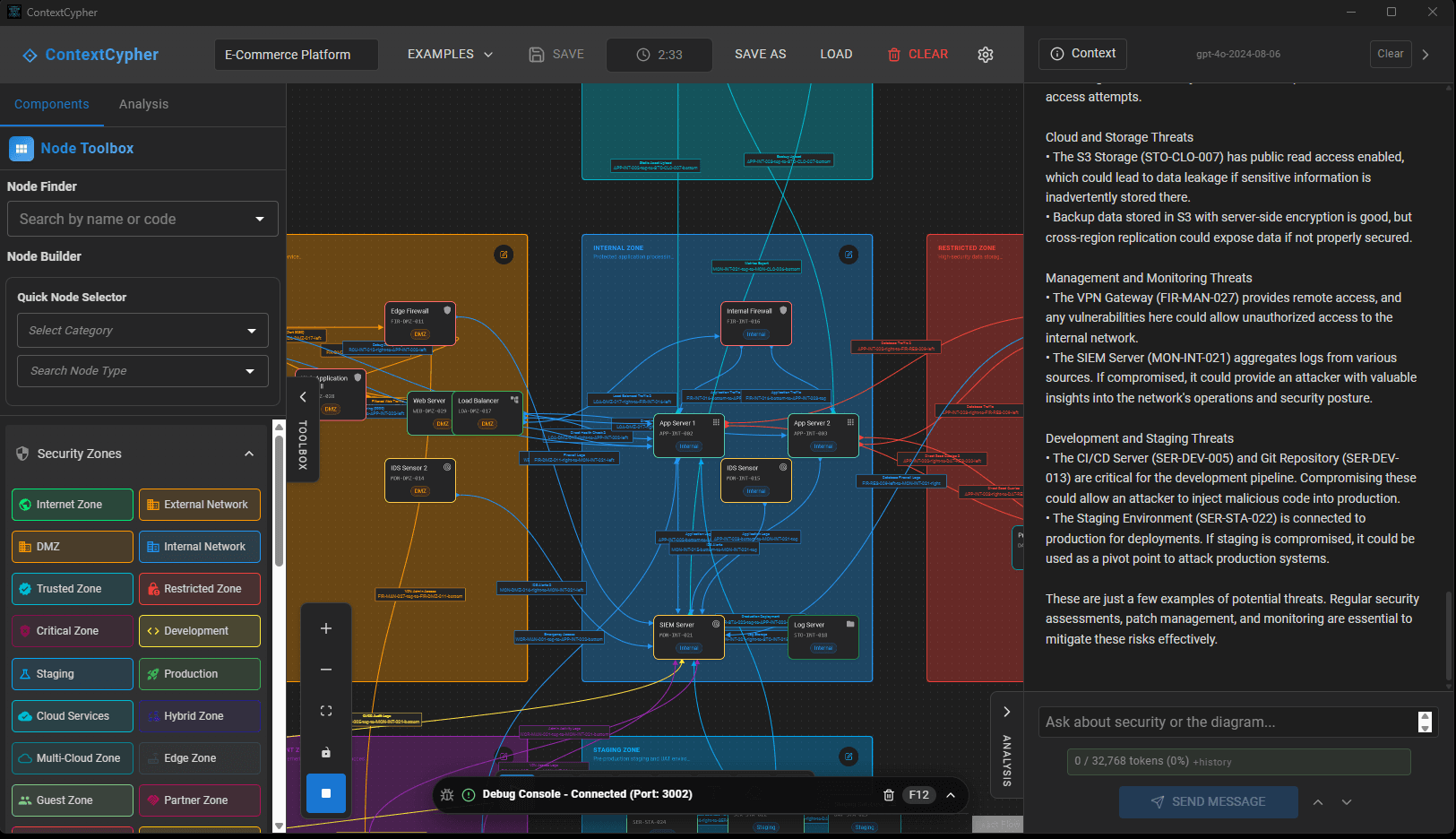
Image 1 – Main dashboard
It is quite clear to anyone who has worked in this area straight away how the application functions. There is a “Node Toolbox” on the left hand side that can be used to develop architecture diagrams for various different types of environments. There are about 30 different types of security zones such as Development, DMZ, Internet Zone, Cloud Services etc. that can be used to construct an architecture diagram. The security components contains all the usual suspects:- Firewall, VPN Gateway, IDS, IPS, SIEM, WAF etc. The OT/SCADA section contains PLC, HMI, Historian etc. Overall, it’s a decent app to easily manually build an architecture diagram for your organisation or upload one that you already have.
Security Analysis
The real power in this application though comes from applying the AI. The goal is to reduce / remove the manual effort required to complete a full risk assessment. Once you have an architecture diagram uploaded (or are testing with the 20+ examples built in which is what I did), then this is when the AI benefits really kick in. There is a tab called “Analysis” which leverages the AI to complete a threat analysis based on the provided architecture diagram. Obviously, the more context that has been provided then the better results returned, e.g. software versions, system configurations etc. The automated analysis takes a couple of minutes. The results look like this:
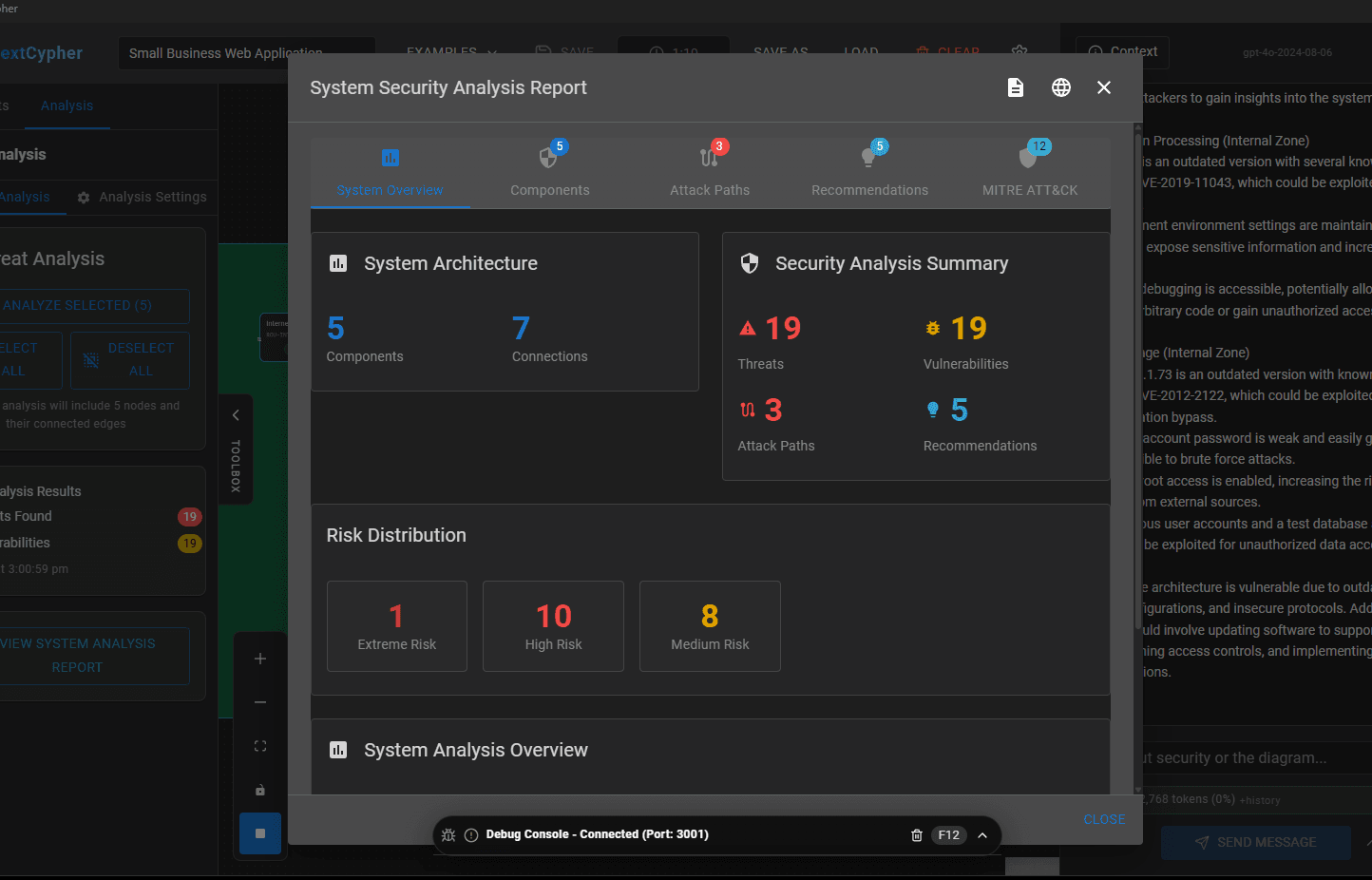
Image 2 – System Overview
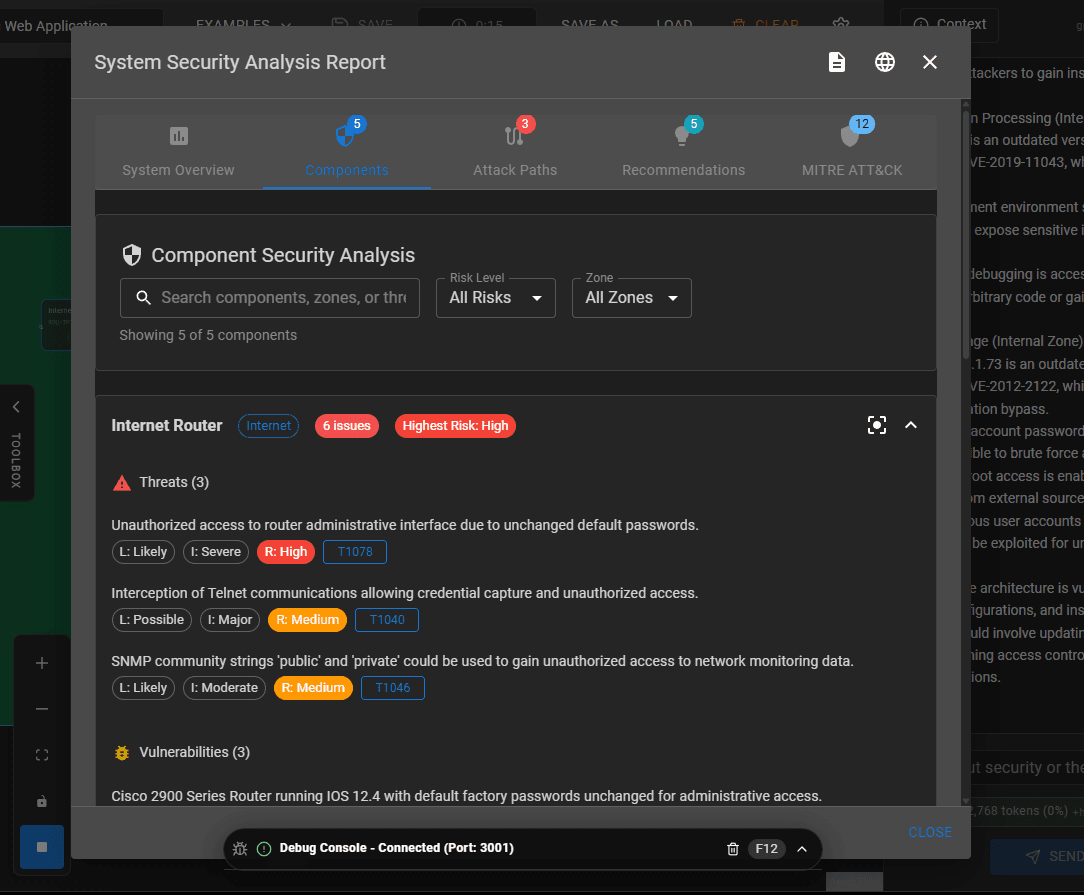
Image 3 – Components
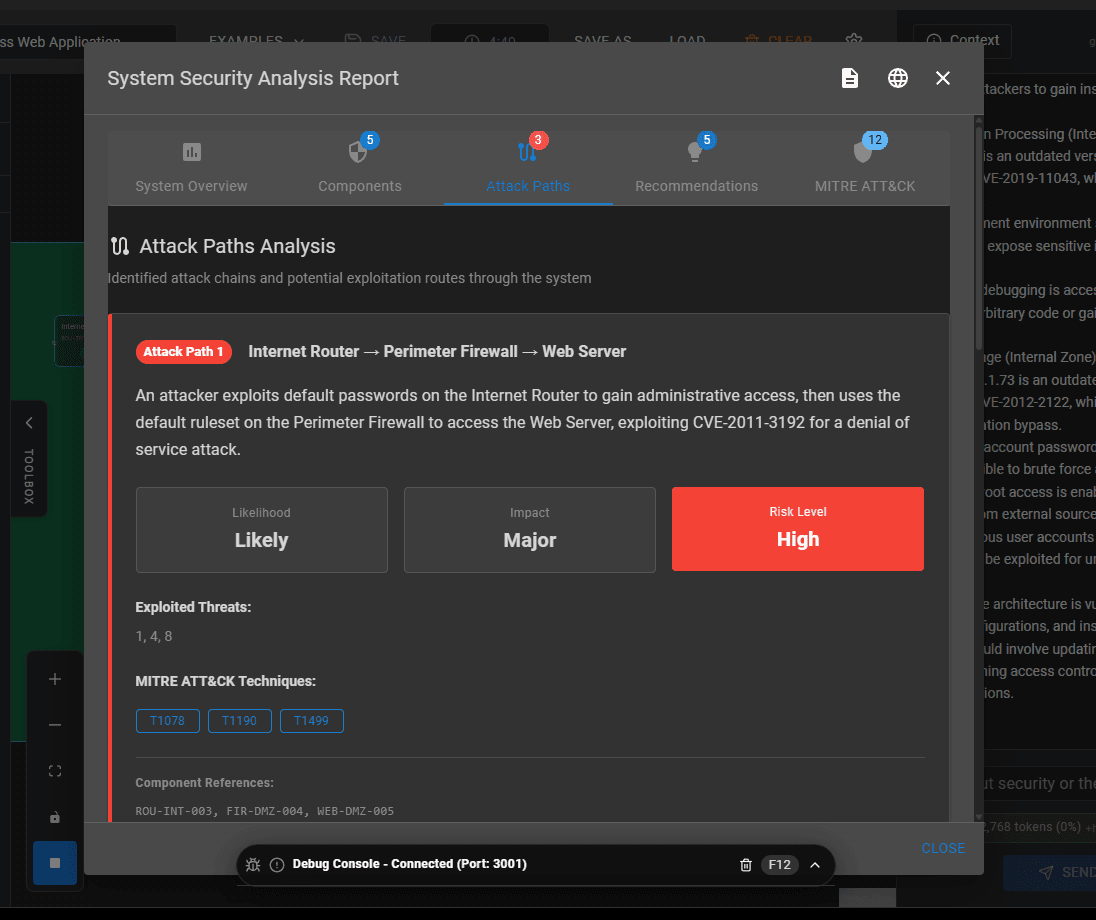
Image 4 -Attack Paths
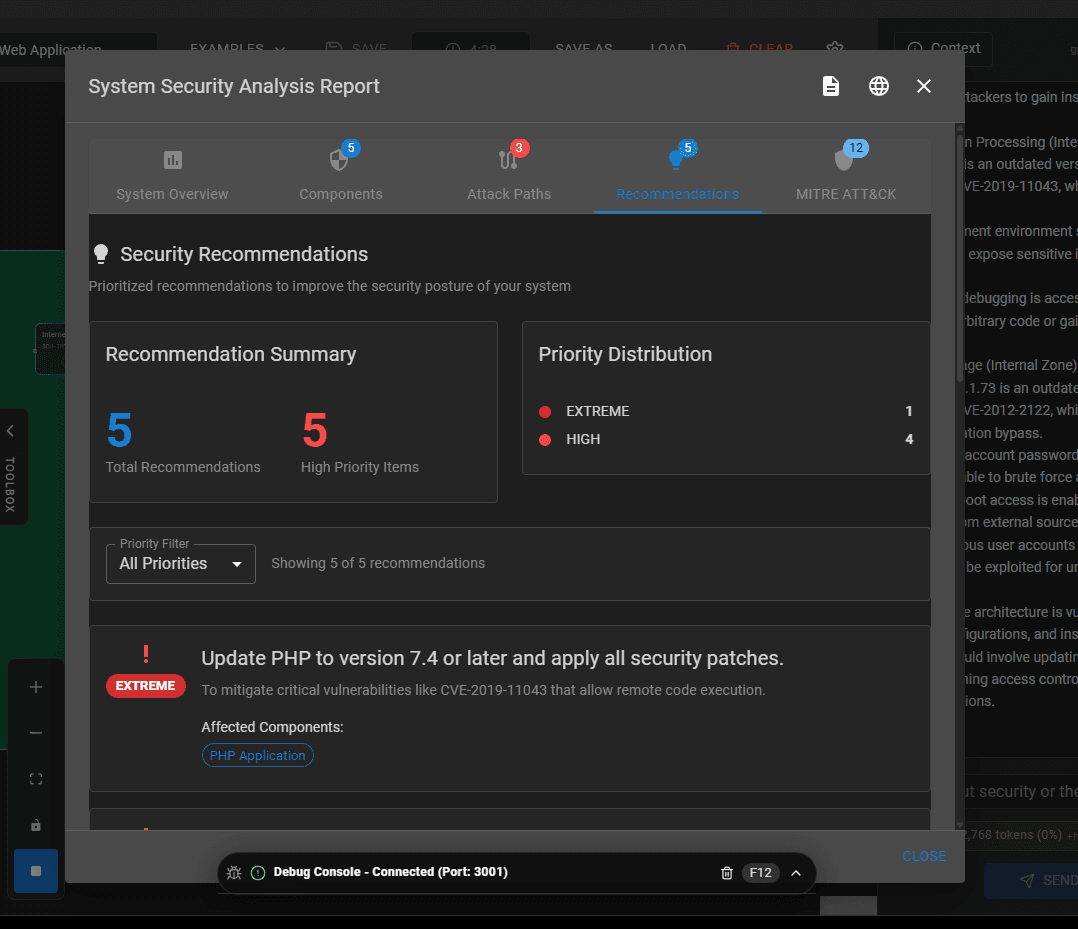
Image 5 – Recommendations
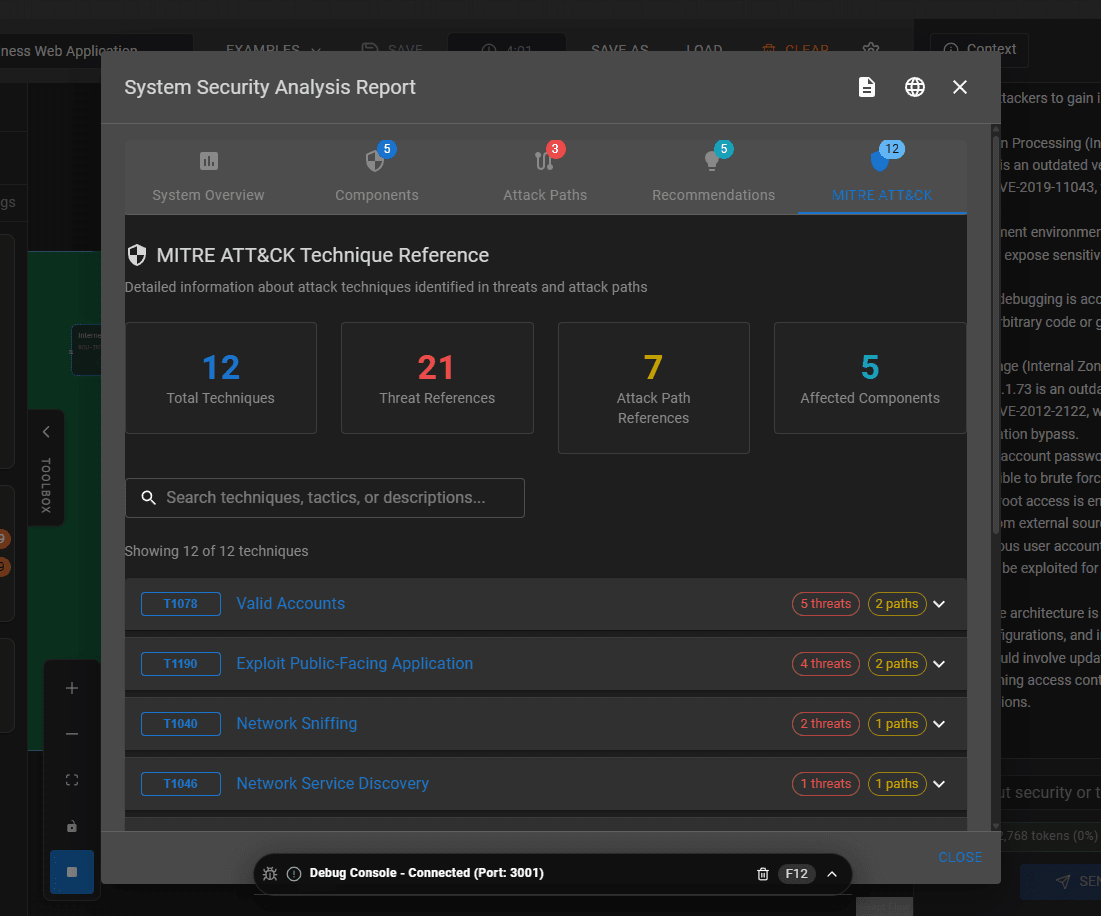
Image 6 – MITRE ATT&CK
The results are impressive. I really like the attack paths feature and the MITRE ATT&CK information is brilliant. I’ve seen organisations complete this manually in the past. It’s not pretty, fun or time efficient so it’s great to see this type of thing completed by AI.
Downsides
AI can only work with the information that is provided to it. Garbage in, Garbage out as they say so it’s really important that the AI has all the relevant context and data to be able to get to the right conclusion, i.e. has all the threat and vulnerability information included. For those that regularly use LLMs, you will know that they almost always do not have up to date information. In security, Up to date information is essential so an application like this is going to need threat intel feeds and real time vulnerability information to deliver value. If it does not know about the latest CVEs etc. then it is not going to report on them.
Really useful use cases
Aside from the obvious automated threat and risk assessment, here are some really useful use cases that I can think of:
1. Automated Architecture diagram generation
If this tool has a spreadsheet full of vulnerability information (e.g. output from a vulnerability scanner), then it can use that information to reverse engineer the architecture diagram and generate one on the fly. This would have been so handy on many security consulting engagements that I’ve been on in the past. For many organisations, this will be a game changer, allowing them to see the big picture and understand how data flows through their organisation and networks.
2. Governance, Risk and Compliance
This app assesses the likelihood and impact of each threat that it identifies. Whilst not directly a GRC tool, this app does apply context and the “High risks” that it identifies are not High risks that one would see in a vulnerability scanner. It considers risks to be high due to the fact that there is a high likelihood of compromise to a critical system, not because is CVSS above 7.0. The risks that this tool identifies can be copied straight into a GRC type tool without the need to apply context by a security expert, or at least the expert has less work to do reviewing the output from the AI to determine whether they agree or not. The benefit to most organisations with limited resources is it helps them to focus those limited resources on the most critical issues first.
3. Incident Response Planning
The Attack Paths and MITRE ATT&CK information provided by the AI in this tool is really useful as many organisations now perform this activity and it is mostly manually, unfortunately. These attack paths, once documented, are also invaluable in designing incident response testing activities and red teaming exercises.
Conclusion
Overall, the AI-Threat-Modeler is a valuable tool for organizations looking to enhance their cybersecurity defenses by providing detailed insights into their network architecture and potential security risks. For many, it will demystify the complexities of network security, provide actionable insights and empower them to take control of their security posture. As an aside, it is also a fantastic educational tool for anyone looking to skill up on cybersecurity, especially threat and risk analysis. I highly recommend giving this tool a try.
I believe this is a low cost tool as Alex is in startup mode and this is pre-seed etc. For anyone looking to jump on the Beta or get access to an early version, I’d recommend reaching out to Alex over at TVS:
https://threatvectorsecurity.com/contact/
